Network
From Hackerspace Brussels
Contents
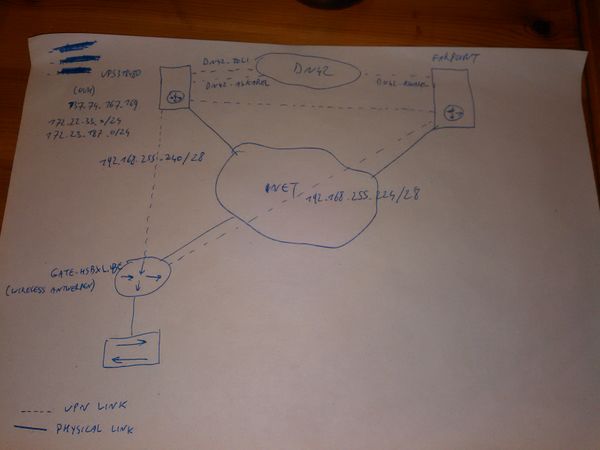
Network structure
Network nodes
Network areas
- in.hsbxl.be - Network inside HSBXL
- out.hsbxl.be - Network segment for off-site events or migration periods
Network services
Address pools
We have the following pools allocated to us:
- IPv4:
- 172.22.33.0/24 dn42
- 172.23.187.0/24 dn42
| Subnet | Machine usage | Description |
|---|---|---|
| 172.22.33.0/29 | ds9 | Interlink with DN42 peers |
| 172.22.33.8/29 | farpoint | Interlink with DN42 peers |
| 172.22.33.16/29 | Gate | DN42 NAT pool |
| 172.22.33.24/29 | MiniGate | DN42 NAT pool |
| 172.22.33.32/27 | Gate | DN42 Server pool |
| 172.22.33.64/27 | ds9 | OpenVPN members pool |
| 172.22.33.96/27 | Gate | SpaceFED wifi |
| 172.22.33.128/27 | Gate | Wired LAN |
| 172.22.33.160/29 | ||
| 172.22.33.168/29 | ||
| 172.22.33.176/29 | ||
| 172.22.33.184/29 | ||
| 172.22.33.192/27 | Gate | IPv4-only LAN |
| 172.22.33.224/29 | ||
| 172.22.33.232/29 | ||
| 172.22.33.240/29 | ds9 | STATIC_IPSEC pool, strongswan VTI-based - NEW |
| 172.22.33.248/29 | ds9 | INTERCONNECT_VPN pool, OpenVPN-based - TO DECOMISSION |
| 172.23.187.0/25 | Gate | WiFi_WPA pool |
| 172.23.187.128/25 |
- 185.18.150.22 (gate.hsbxl.be (Wireless Antwerpen))
- 137.74.167.169 (vps318480.hsbxl.be (OVH))
- IPv6:
-
2001:6f8:147f::/48 (SixXS)PoP has disappeared: subnet and tunnels are permanently gone - 2001:470:7d73::/48 (TunnelBroker.net)
- 2001:470:1f14:cc0::2 (gate.hsbxl.be (TunnelBroker.net))
- 2001:41d0:302:2100::1d46 (vps318480.hsbxl.be (OVH))
-
IPv4 public address policy
The following ports/protocols will NOT be forwarded from the internet to a client inside the network. Negociation is not possible.
- TCP: 22, 23, 25, 53, 80, 111, 137, 138, 139, 179, 443, 389, 587, 631, 636
- UDP: 53, 111, 137, 138, 139, 500, 631, 1337, 1812, 1813, 4500
- Protocols: 41, 50, 51
Reasons:
- TCP 22: Used for network device access from outside
- TCP 23: Banned for security reason
- TCP 80, 443: We have a better solution than stupid port forwarding: a reverse proxy is configured to connect to your web service. You can ask as many hosts as you like, they will be forwarded as required. You don't even need to worry about SSL: we do SSL off-loading for you.
- TCP/UDP 53: Used for our DNS. Just ask if you need a subdomain
- TCP/UDP 111, 137, 137, 139: Those file sharing protocols are banned for security reason.
- UDP 500, 4500: Used for IPSEc
- UDP 1812, 1813: RADIUS authentication
Address allocations
The subnets are broken down in smaller blocks allocated to the following zones:
- in.hsbxl.be: 2001:470:7d73::/52
- out.hsbxl.be: 2001:470:7d73:1000::/52
- Interconnect LAN: 2001:470:7d73:ffff::/52
We are also using the following pools internally (only on our internal gateway). This won't be announced to DN42 over BGP, but is announced internally over OSPF
- IPv4
- 192.168.222.0/24 (HSBXL internal non-routable LAN)
- 192.168.222.0/26 (HSBXL no-internet)
- 192.168.222.64/26 (Sidekick for main site - OOB management)
- 192.168.9.0/24 (Public WiFi, non routable)
- 192.168.255.0/26 (Routing devices addresses, internally routed)
- 192.168.255.1/32 - vps318480.hsbxl.be
- 192.168.255.2/32 - gate.in.hsbxl.be
- 192.168.255.3/32 - farpoint.hsbxl.be
- 192.168.255.4/32 - gate2.in.hsbxl.be
- 192.168.255.5/32 - minigate.out.hsbxl.be
- 192.168.255.64/26 (anycast addresses)
- 192.168.255.64/32 (test - for internal services)
- 192.168.255.65/32 FUTURE: Internal RADIUS/LDAP server - READ ONLY ACCESS
- 192.168.255.67/32 FUTURE: Forward proxy
- 192.168.255.192/26 (Stub tunnels range)
- 192.168.222.0/24 (HSBXL internal non-routable LAN)
VLANs
This is the current VLAN layout. This layout is kept across sites. All ports on the switches have descriptions in the config
BottomSwitch#show interfaces description Interface Status Protocol Description Vl1 up up Vl1000 admin down down Fa0/1 down down Thinclient 1 Fa0/2 down down Thinclient 2 Fa0/3 down down 42 Fa0/4 down down Fa0/5 down down 42 Fa0/6 down down Electronic lab table switch Fa0/7 down down 42 Fa0/8 down down 42 Fa0/9 down down 42 Fa0/10 down down 42 Fa0/11 down down 42 Fa0/12 down down 42 Fa0/13 down down 42 Fa0/14 down down 42 Fa0/15 down down Fa0/16 down down Fa0/17 down down 42 Fa0/18 down down 42 Fa0/19 down down 42 Fa0/20 down down 42 Fa0/21 down down 42 Fa0/22 down down 42 Fa0/23 down down 42 Fa0/24 down down 42 Fa0/25 down down 42 Fa0/26 down down 42 Fa0/27 down down Rpi-hosting Fa0/28 down down Rpi-hosting Fa0/29 down down Rpi-hosting Fa0/30 down down Rpi-hosting Fa0/31 down down Unifi 1 Fa0/32 down down Unifi 2 Fa0/33 down down Unifi 3 Fa0/34 down down Unifi 4 Fa0/35 up up SIP phone Fa0/36 up up HAL9000 Fa0/37 down down "dot1x experimental" Fa0/38 down down Printer Fa0/39 admin down down Proxmox LAN Fa0/40 down down "VoIP dedicated VLAN" Fa0/41 down down Zoppas Fa0/42 up up RIPE ATLAS Fa0/43 down down Ground floor Fa0/44 down down 1stfloor and Falisse camera Fa0/45 up up Schizophreniac hypervisor Fa0/46 down down 3rd floor neighbour Fa0/47 up up OOB MGMT Fa0/48 up up TRUNK to Gate Gi0/1 down down Gi0/2 down down BottomSwitch#
The VLAN numbering is divided in several groups:
- <10: Wireless networks and legacy allocation
- 1x, 1xx: Whole floor allocation: x=Floor number
- 1xyy: Customer allocation: x=floor number, y=client number
- 2x: Internet uplink(s)
- 3x: Application-specific VLANs
- 42: Legacy flat LAN
- 5x: RADIUS-assigned VLANs for WiFi
| VLAN ID | Description | Infos |
|---|---|---|
| 3 | Wireless Antwerpen Uplink | |
| 4 | Servers LAN | |
| 6 | IPv6 only net | Also carries the HSBXL-v6 SSID |
| 7 | SpaceFED | Not sure if it will be kept |
| 8 | WiFi WPA | HSBXL SSID |
| 9 | WiFi public | HSBXL-public SSID, Open to all |
| 10 | Ground floor network | Currently unused |
| 11 | 1st floor network | In use. |
| 12 | 2nd floor network | Currently unused |
| 13 | 3rd floor network | Used by our donstairs neighbour: KOBALT |
| 42 | Our wired LAN | |
| 44 | IPv4 only network | Sparsely available. HSBXL-v4 SSID |
| 58 | RADIUS-assigned members VLAN | |
| 59 | RADIUS-assigned guest VLAN | |
| 666 | Proxmox cross-site BIGLAN | One broadcast domain potentially covering several physical locations |
WiFi
- 3 Unifis access points are broadcasting the HSBXL, HSBXLv6 and HSBXL-PUBLIC SSIDs, Powered by the ToughSwitch.
- One nanostation is our Wireless Antwerpen link, Powered by the ToughSwitch.
PEN/OID
We have the following PEN from IANA: 1.3.6.1.4.1.43666.